For years, the cybersecurity landscape has operated under a stark assumption: the Dark Web is a secure, anonymous sanctuary for cybercriminals. It’s where stolen data is traded, malware is rented, and threat actors operate with perceived impunity, shielded by layers of encryption and secrecy. That foundational myth was fundamentally shattered in January 2026.
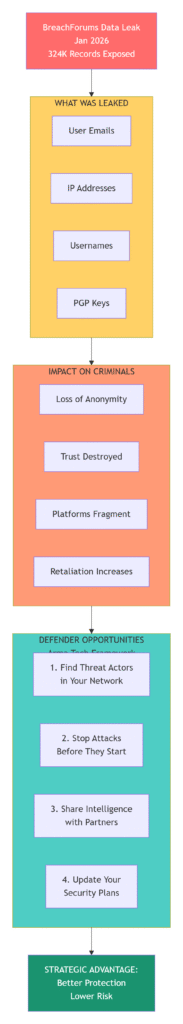
A catastrophic data leak from BreachForums, one of the most prominent and resilient cybercrime marketplaces on the Dark Web, exposed nearly 324,000 user records. This event didn’t just breach a forum; it breached the illusion of invincibility that sustains the digital underground. As analysts from Resecurity confirmed, this incident underscores a pivotal truth: Data breaches are an omnipresent risk, and cybercriminal ecosystems are often just as vulnerable if not more so than the enterprises they target.
For cybersecurity defenders, threat intelligence teams, and CISOs, this disruption is not just news, it’s a strategic opportunity. This deep-dive analysis from Arma Tech will unpack the BreachForums leak, explore its far-reaching implications, and provide an actionable framework for turning underground chaos into a tangible defensive advantage.
Understanding BreachForums: The Cybercrime Hub That Fell
To grasp the magnitude of this leak, one must first understand what BreachForums represented. Emerging in 2022 as the direct successor to the seized RaidForums, BreachForums quickly consolidated power as a central nervous system for the cybercrime underworld. It was more than a forum; it was a marketplace, a collaboration platform, and a news source for threat actors globally.
Key Functions of BreachForums Included:
- Data Trading: A primary marketplace for buying and selling massive SQL databases, credentials, and Personally Identifiable Information (PII).
- Extortion Coordination: A known hub for ransomware groups and data extortion actors to name victims, leak samples, and negotiate.
- Tooling and Services: Access to malware-as-a-service (MaaS), exploit kits, hacking tutorials, and bulletproof hosting.
- Community and Reputation: A space where threat actors built reputations (through “stars” and feedback) and formed alliances.

The platform employed robust operational security (OpSec) measures: rotating clearnet domains, persistent Tor hidden services, aggressive DDoS protection, and strict invitation protocols. It survived multiple law enforcement actions, including the arrest of its former administrator and persistent targeting by global agencies. Its downfall in January 2026 wasn’t due to a police raid, it was the result of internal infrastructure failure and poor security hygiene, a stark lesson for any organization.
The January 2026 Breach: A Forensic Breakdown of the Exposed Data
According to a detailed analysis by Resecurity’s HUNTER unit, the leaked database originates from BreachForums’ core backend systems. The exposure of 323,986 user records provides an unprecedented look inside the criminal ecosystem.
The leaked dataset includes the following critical fields:
- Usernames & Aliases: The primary handles of forum members, including high-ranking actors.
- Email Addresses: Both clear-text and obfuscated addresses are used for registration and communication.
- Argon2-Hashed Passwords: While hashed, these are not immune to cracking campaigns, especially if passwords are weak or reused.
- IP Addresses (Historical): Potentially the most damaging exposure, compromising the anonymity of users who may have lapsed in using VPNs or Tor.
- Registration Timestamps: Allowing for timeline analysis and correlation with external events.
- Associated PGP Keys: Cryptographic identities used for secure messaging and verifying posts, whose exposure can break trust chains.
High-Value Targets Within the Data:
The leak is particularly damaging because it isn’t limited to low-tier users. It includes records linked to:
- Forum Administrators and Moderators
- Notorious Threat Actors and Data Breach Sellers
- Affiliates of Major Ransomware-as-a-Service (RaaS) Programs
- Initial Access Brokers (IABs)
Early geographic analysis of the exposed IP data shows significant concentrations in the United States, Germany, the Netherlands, France, Turkey, and the United Kingdom, highlighting the global scale of the platform’s user base and the subsequent investigative fallout.
The Ripple Effect: Why This Leak is a Strategic Turning Point
The collapse of trust within a major criminal platform creates seismic waves across the threat landscape. This breach signals a fundamental shift with multiple downstream effects.
1. The Fragmentation of Threat Actor Communities:
Trust is the currency of the Dark Web. When a platform proves insecure, its user base scatters. We anticipate a migration to alternative forums (like Exploit, Cracked, or new iterations), increased use of encrypted messenger platforms (Telegram, Discord), and the rise of smaller, more private invitation-only groups. This fragmentation makes broad monitoring more challenging but can also lead to operational security mistakes during migration.
2. Intra-Criminal Retaliation and “Doxxing” Waves:
Exposed actors are now vulnerable. We expect a surge in retaliatory actions, including:
- Account takeovers on other platforms using exposed credentials.
- “Doxxing” campaigns where adversaries expose each other’s real identities.
- Phishing campaigns target the exposed email addresses, leveraging the fear and confusion.
3. A Goldmine for Law Enforcement and Threat Intelligence:
For investigators, this dataset is a treasure trove. Cross-referencing these emails, IPs, and aliases with:
- Existing breach corpora (e.g., Constella Intelligence, HaveIBeenPwned)
- Law enforcement databases
- Internal Security Information and Event Management (SIEM) logs
…can lead to concrete attribution, disruption of active operations, and preemptive arrests.
4. A Stark Reminder of Universal Vulnerability:
This event is a powerful narrative tool for security awareness. It demonstrates that no system is inherently secure—not even those operated by security-paranoid criminals. This reinforces the need for relentless security hygiene, even in the most sensitive environments.
The Arma Tech Framework: Leveraging Underground Disruption for Proactive Defense
At Arma Tech, we advocate for an intelligence-driven security posture that capitalizes on moments of adversary weakness. Here is a step-by-step framework for transforming this event into defensive action.
Phase 1: Intelligence Acquisition and Enrichment
- Acquire the Dataset (Ethically): Obtain the leaked data through trusted threat intelligence feeds or dark web monitoring services. Never engage directly with criminal forums.
- Enrich and Cross-Reference: Use internal and external tools to enrich the exposed data. Match emails and IPs against:
- Your organization’s past incident response logs.
- VPN and proxy exit node lists.
- Credential stuffing attack attempts captured in your SIEM.
- Third-party breach databases to find password reuse patterns.
Phase 2: Internal Defense Posture Adjustment
- Update Threat Hunting Playbooks: Create new hunts focused on IOCs from this leak. Hunt for traffic from exposed IP ranges or login attempts using exposed usernames/emails.
- Enhance Credential Monitoring: If any exposed email domains belong to your organization, force password resets and implement stringent multi-factor authentication (MFA) checks. Scan for these credentials in your own leaked credential repositories.
- Increase Alerting for Follow-On Attacks: Heighten vigilance for phishing campaigns that may leverage this leak as a lure (e.g., “Your BreachForums data was leaked, click here to see.).
Phase 3: Proactive Threat Landscape Reshaping
- Feed Intelligence to Your Ecosystem: Share validated, anonymized indicators with your industry’s Information Sharing and Analysis Center (ISAC) and trusted peer groups.
- Stress-Test Your Incident Response (IR): Use this scenario in a tabletop exercise. How would your IR team respond if an executive’s email were found in this dump? How would communications and legal teams handle it?
- Refine Your Threat Model: Incorporate “criminal infrastructure collapse” as a scenario. How would a major forum takedown impact the threat groups targeting your sector?
Long-Term Strategic Implications for Cybersecurity Leaders
For the C-suite and board members, this breach transcends technical details. It speaks to core strategic realities:
- The Blurring Line Between Defensive and Offensive Intelligence: The most effective defense now requires understanding the attacker’s world, their tools, and their points of failure.
- The Necessity of Proactive Threat Intelligence: A passive, compliance-driven security program will miss these opportunities. Investing in active threat intelligence is no longer optional; it’s a critical competitive (and defensive) advantage.
- The Human Element of Cyber Risk: This leak exposes the people behind the attacks. Security awareness training must evolve to discuss the human infrastructure of cybercrime, making the threat more tangible and real for employees.
Conclusion: Seizing the Moment of Adversary Weakness
The BreachForums leak of January 2026 is a landmark event. It proves that the walls of the digital underground can crumble from within, victims of the same poor security practices they exploit in others.
For the vigilant defender, this is not a time for schadenfreude, but for action. It is a unique window of heightened visibility into the adversary’s camp a moment when their OpSec is compromised, their communities are in disarray, and their focus is divided.
At Arma Tech, we build cybersecurity solutions grounded in this intelligence-driven reality. We believe true resilience comes not just from defending your perimeter, but from understanding the forces arrayed against it, and striking strategic advantages when they present themselves. In the ongoing battle for digital security, knowledge of your enemy, especially when they are at their weakest, is your most powerful weapon.
Ready to transform threat intelligence into actionable defense? Contact Arma Tech today to learn how our cyber intelligence and proactive defense platforms can help your organization anticipate, adapt, and respond to an evolving threat landscape.