Proton research uncovers 300 million stolen credentials on the dark web. Learn how this credential theft fuels data breaches and how to protect your business.

Stolen credentials have become the silent epidemic fueling modern corporate breaches. A groundbreaking report from Proton, the Swiss-based security leader, has uncovered a massive cache of over 300 million stolen credentials circulating on dark web cybercrime markets. The findings reveal that approximately half of these records include passwords, providing tangible evidence of the staggering scale of the credential theft crisis that’s reshaping corporate security worldwide.
The Direct Link Between Stolen Credentials and Soaring Data Breach Costs
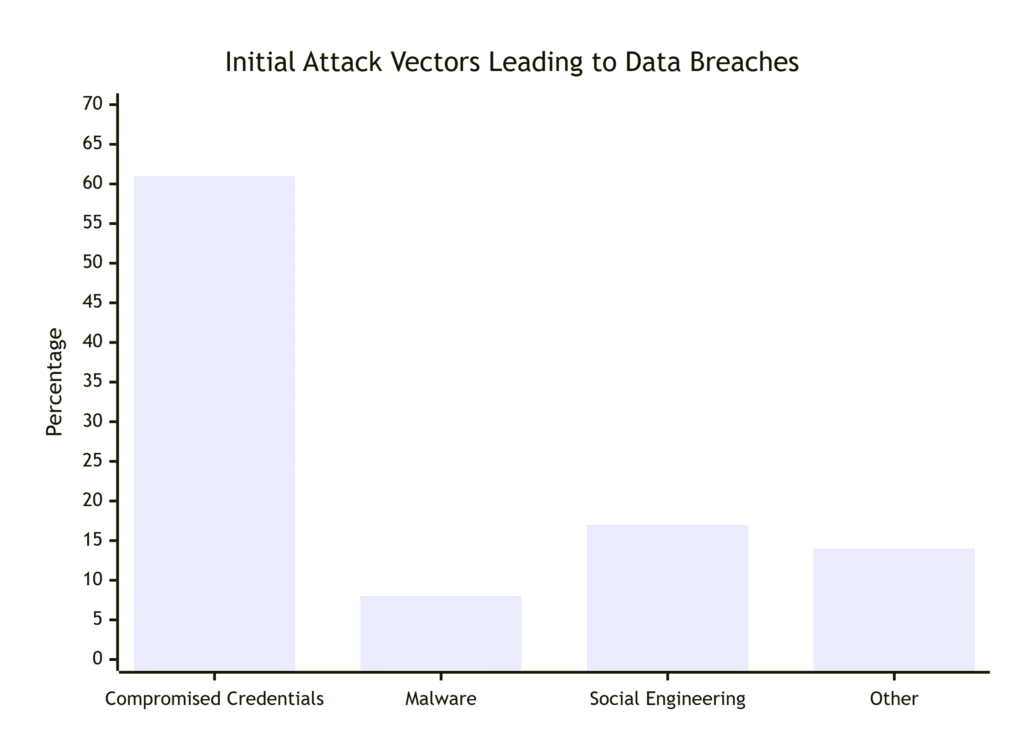
This research underscores a critical reality in cybersecurity: stolen credentials have become the primary enabler of costly data breaches. According to an industry-wide Verizon report, compromised credentials are the root cause of 61% of all confirmed data breaches globally.
The financial repercussions are severe. A single breach stemming from stolen credentials costs a company an average of $4.88 million, according to IBM’s “Cost of a Data Breach Report.” Beyond the immediate financial loss, organizations face an average operational disruption lasting between 21 and 40 days as they work to contain the incident, eradicate the threat, and recover their systems.
Stolen Credentials: The Dominant Attack Vector in Modern Cyber Threats
The following chart illustrates how credential theft has become the dominant attack method, far surpassing other vectors like malware or social engineering.
An Evolving Threat Landscape Fueled by Stolen Credentials
The Proton report identifies the most targeted sectors for stolen credentials, with finance, healthcare, and cloud SaaS (Software-as-a-Service) providers at the forefront. The primary target for entry, however, remains email services.
“Email is the key to the kingdom,” the report states. “It is the central hub for authentication resets, financial recovery mechanisms, and critical business communication. Compromising an email account is often all an attacker needs to cascade through a victim’s digital life and, by extension, a corporate network.”
The research concludes that organizations relying on email-based authentication without multi-factor authentication (MFA) are at exceptionally high risk. Other significant vulnerabilities include maintaining dormant accounts of former employees and allowing the use of unsecured personal devices for work purposes.
Shifting Security Strategy: Neutralizing the Threat of Stolen Credentials
In response to these findings, security experts are urging a fundamental shift in strategy. Because attackers are “logging in” with stolen credentials rather than “breaking in,” traditional perimeter-based defenses are no longer sufficient.
“The security perimeter is now identifying itself,” the report argues. This necessitates layered controls designed to neutralize the value of stolen credentials, including:
Proactive dark web monitoring: Scans for exposed employee credentials to enable preemptive action.
Universal enforcement of Multi-Factor Authentication (MFA): Renders a stolen password useless on its own.
Enterprise password vaults: Empower employees to use and manage strong, unique passwords for every service.
Privileged Access Management (PAM): Secures highly sensitive system roles and administrative accounts.
The following chart illustrates how credential theft has become the dominant attack method, far surpassing other vectors like malware or social engineering:
Bar chart showing stolen credentials as the top cause of data breaches at 61%.
Shifting Security Strategy: Neutralizing the Threat of Stolen Credentials
In response to these findings, security experts are urging a fundamental shift in strategy. Because attackers are “logging in” with stolen credentials rather than “breaking in,” traditional perimeter-based defenses are no longer sufficient.
“The security perimeter is now identifying itself,” the report argues. This necessitates layered controls designed to neutralize the value of stolen credentials, including:
- Universal enforcement of Multi-Factor Authentication (MFA): Renders a stolen password useless on its own.
- Enterprise password vaults: Empower employees to use and manage strong, unique passwords for every service.
- Privileged Access Management (PAM): Secures highly sensitive system roles and administrative accounts.
- Proactive dark web monitoring: Scans for exposed employee credentials to enable preemptive action.
The Future of Protection: Moving Beyond Stolen Credentials
The future of protection, according to the report, lies in moving toward passwordless authentication systems, such as passkeys and biometrics, which are inherently resistant to theft.
Final Assessment: The Concrete Reality of Stolen Credentials
The uncovering of 300 million stolen credentials is not an abstract threat but a concrete measurement of the current risk landscape. For businesses, it serves as a direct call to action to fortify their identity and access management protocols before their own credentials appear in the next dark web dataset.
At Arma Technology, we are committed to being your guide and partner in this journey. Our team of experts is here to help you implement these layered defenses, from initial planning and integration to ongoing threat monitoring and response.
Let’s have a conversation about your unique environment and how we can help you build a security posture that is not only strong but also intelligent and adaptive..
Contact Arma Technology today to schedule a confidential security consultation.